


Do you have an e-shop and you've lost data? Or has it been downloaded illegally? You have no control over what happens to them next? Then you have had a security incident. In this article you will find instructions on how to complete a data breach report according to the GPDR.
If you're wondering how to handle a security incident, read our next article ↗.
The form for reporting a security incident can be found here ↗.

First you need to fill in basic identification data. The first section is the administrator. This is the person who determines the purposes and means of processing. In the case of an e-shop, the controller of personal data is usually the e-shop itself. It has decided what data it will process about its customers, what tools it will choose for this purpose, what add-ons it will install, etc. So if you are the e-shop affected by the leak, you fill in your identification data here.
Do you have a data protection officer? This is a specific function that you may know as a DPO. If you don't have one, fill in the contact details of the person who is responsible for GDPR in your organisation.
In the next section, you need to fill in other entities that may be relevant to the security incident. Did the incident occur on the side of the platform provider where you run your e-shop? Fill in the provider's information here.
Indication of the time of the incident. It is particularly important to fill in when you (as administrator) became aware of the breach, as 72 hours are counted from this point. If you missed the 72-hour deadline, you must justify here what the reason was for it happening.

On the next page, you need to describe what the security incident was about, including the impact it had on personal data. We recommend being as specific as possible here so that further steps can be addressed and risks can be properly assessed in cooperation with the Data Protection Authority.
"I don't know exactly what happened, I was only told by the operator of the platform where I have my e-shop that there was an incident."
Did you say that phrase to yourself? Then contact this operator. He should be able to provide you with more detailed information. The operator of the platform where you run your e-shop is most likely the data processor. The processing contract should then state by when they must provide you with the cooperation, what they must tell you, etc.

The form is quite intuitive and it is possible to follow the pre-prepared check-boxes. It is essential to distinguish whether the incident concerns special categories of personal data or only "classic" data.
The special categories of personal data are those listed in point 7 of the form. Please note that, for example, a photograph does not automatically constitute a special category of personal data. Although, for example, biometric information can be read from a photograph to uniquely identify a person, photographs must actually be processed by you to do so. It is therefore normally classified as classic personal data.
In the vast majority of cases, the e-shops will be dealing with classic personal data in the event of an incident. However, if it is a specialised e-shop that collects, for example, health information for individual goods, you may also need to complete section 7.1.
In point 8, you must then select who the personal data relates to, and on the next page in the report you must then fill in the number of people and records affected by the breach.
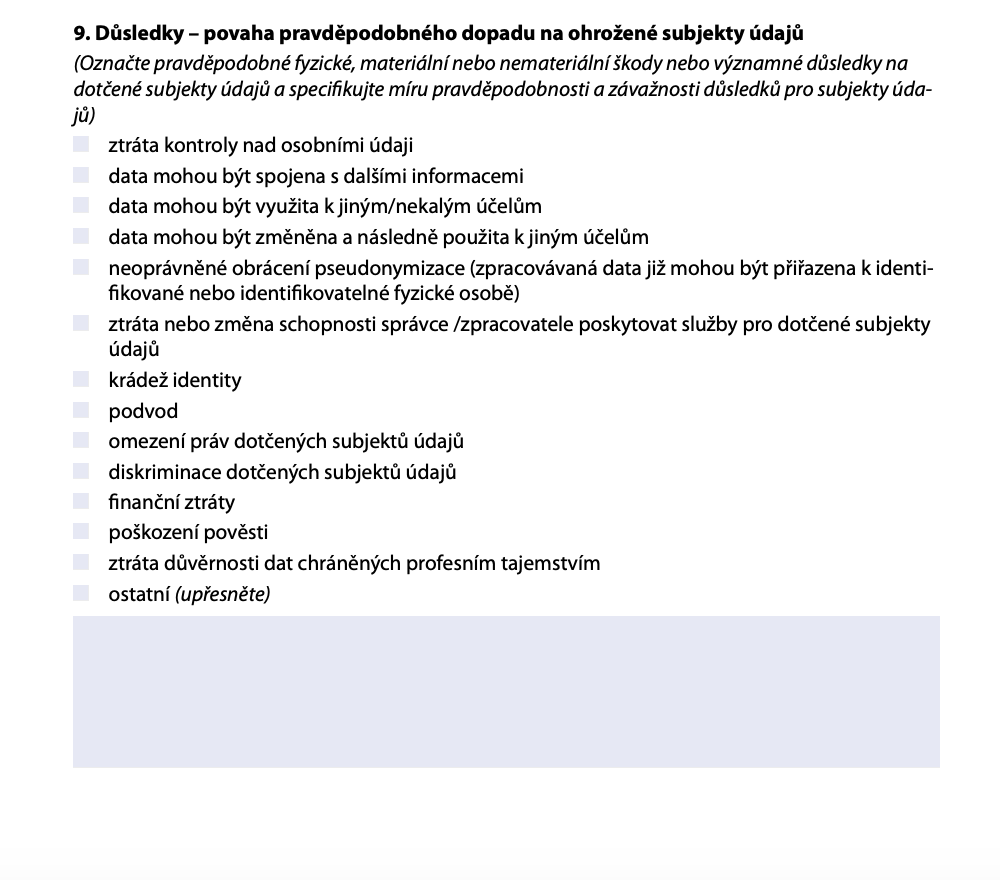
You need to have sufficient information about the security incident. Without it, it would be impossible to determine what impact the incident will have on data subjects.
Again, the rule is that this information should be provided to you by the platform operator or by the party where the incident occurred. In the case of unauthorised downloading of personal data, the most common impact is the loss of control over personal data. But at the same time, the scale of the leak can be so large that it can lead to financial losses, identity theft, etc.
If no external party was involved in the security incident, you as an e-shop must have this information.
Clueless how to determine the consequences? Drop us a line ↗.

Now comes the tricky part. Here we often encounter the fact that there is no internal mapping of how the data is secured and everything is done by eye.
We certainly do not recommend providing false information. It may backfire later. Often, at the very least, you can rely on a processing agreement (if the incident relates to, for example, the operator of the platform where the e-shop is running or the add-on), which also contains information about the security of personal data.
Furthermore, internal data protection guidelines and other internal regulations may be used. Again, the operator, who should have an overview of how the e-shop is secured, can help you technically.
We can prepare the internal documentation for you ↗.

If the security incident was linked to a third party (e.g. a linked service on an e-shop, an e-shop operator), this party should provide you with more detailed information.
If you don't have the information yet and are under a 72-hour deadline, you can leave it blank for now, or add that you will add the information later. This also applies to item 11.3, which you do not have to decide right away. Notification to affected individuals needs to be made when there is a high risk from a security incident. However, you will not assess this without sufficient information.
Would you like advice on whether you need to report to the individuals concerned? Drop us a line ↗.

This point should be completed when the processing also concerns other countries. Typically, when an e-shop is operated in more than one country or when information about people from more than one country is processed. The reason why this section needs to be completed is to identify the lead supervisory authority, as GDPR is based on the one-stop-shop principle.
If you are an e-shop with a primary establishment in the Czech Republic, reporting to the Data Protection Authority will be done as a report to the lead supervisory authority.

At the end of the report, you need to fill in whether the incident involves, for example, a processor from a third country (outside the EU). This is because there are additional risks with such processing and there must be additional supplementary documentation (e.g. standard contractual clauses).
However, this is already such a specific case that, if it occurs, we definitely recommend consulting experts to correctly identify whether a transfer outside the EU is OK.
The form for reporting a security incident is quite intuitive. If you have any problems filling it in, please do not hesitate to write to us.
At the same time, if you are concerned that you don't have all your processes in order, be sure to email us as well. We will check and set up everything ↗.